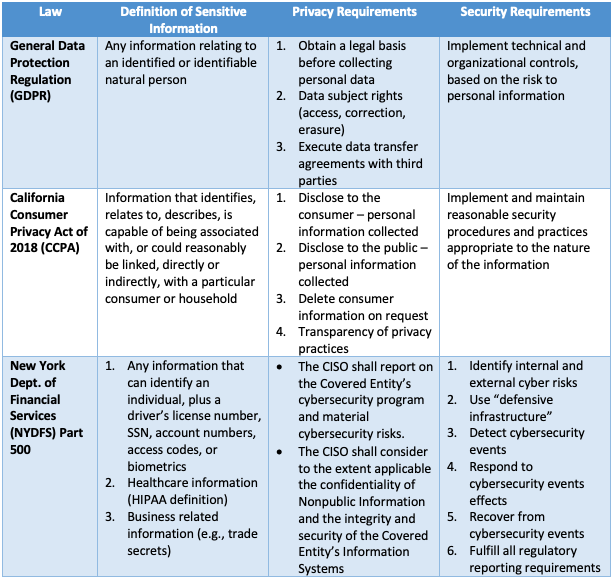
Anonymisation and open data: an introduction to managing the risk of re-identification (report) – The ODI
How personal data flows into Sage CRM - Sage CRM Hints, Tips and Tricks - Sage CRM - Sage City Community
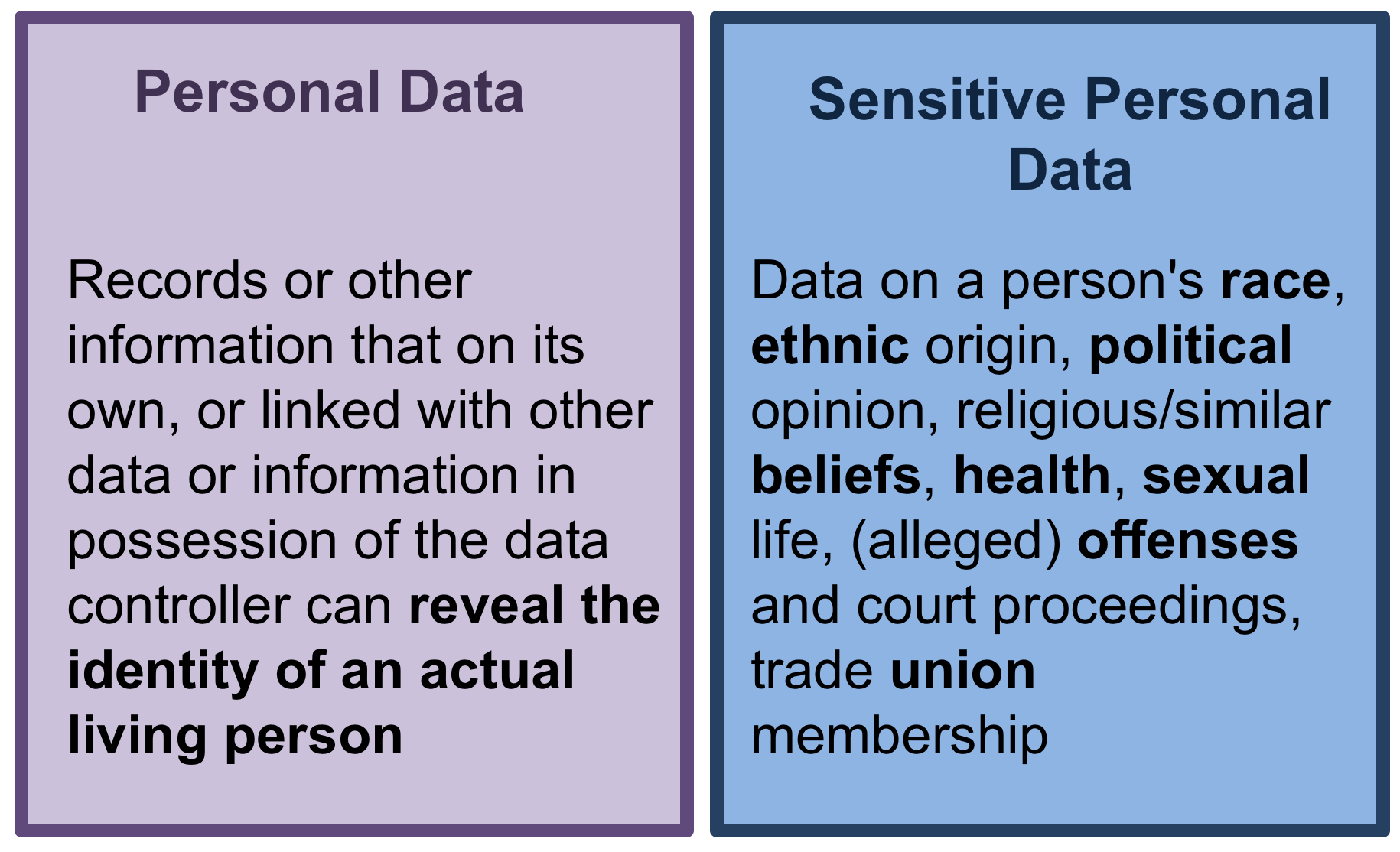
Balancing Ethics and Transparency (part II): publishing sensitive data | Political Science Replication
Go secure yourself: data protection and data security for digital health | by Jovan Stevovic | Towards Data Science

Ground Labs, the sensitive data discovery experts, provide this handy infographic to understand your rights… | Data science learning, Cyber security awareness, Data
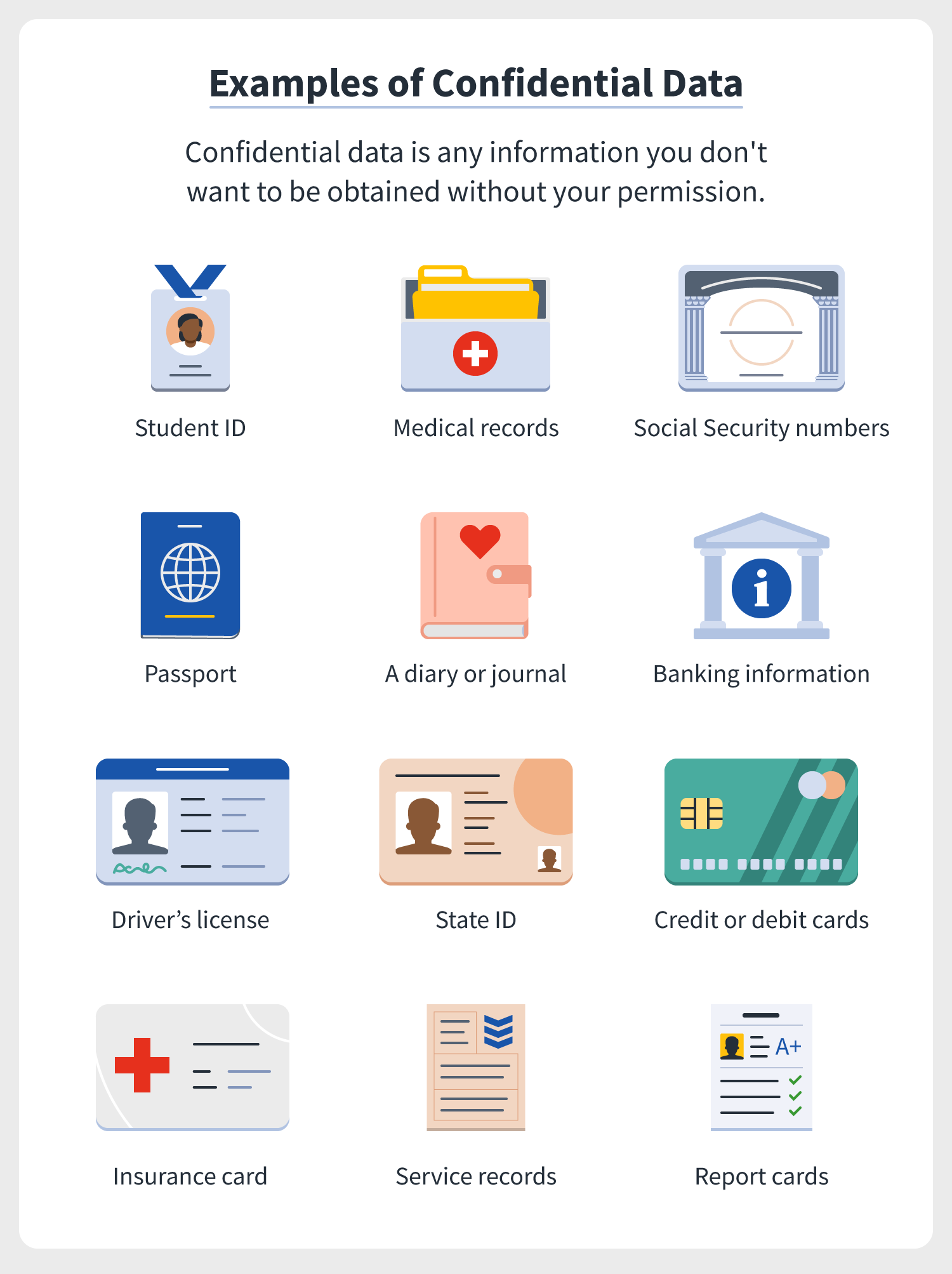
Survey: Majority of Americans put their confidential data on a piece of paper, not the cloud | Norton

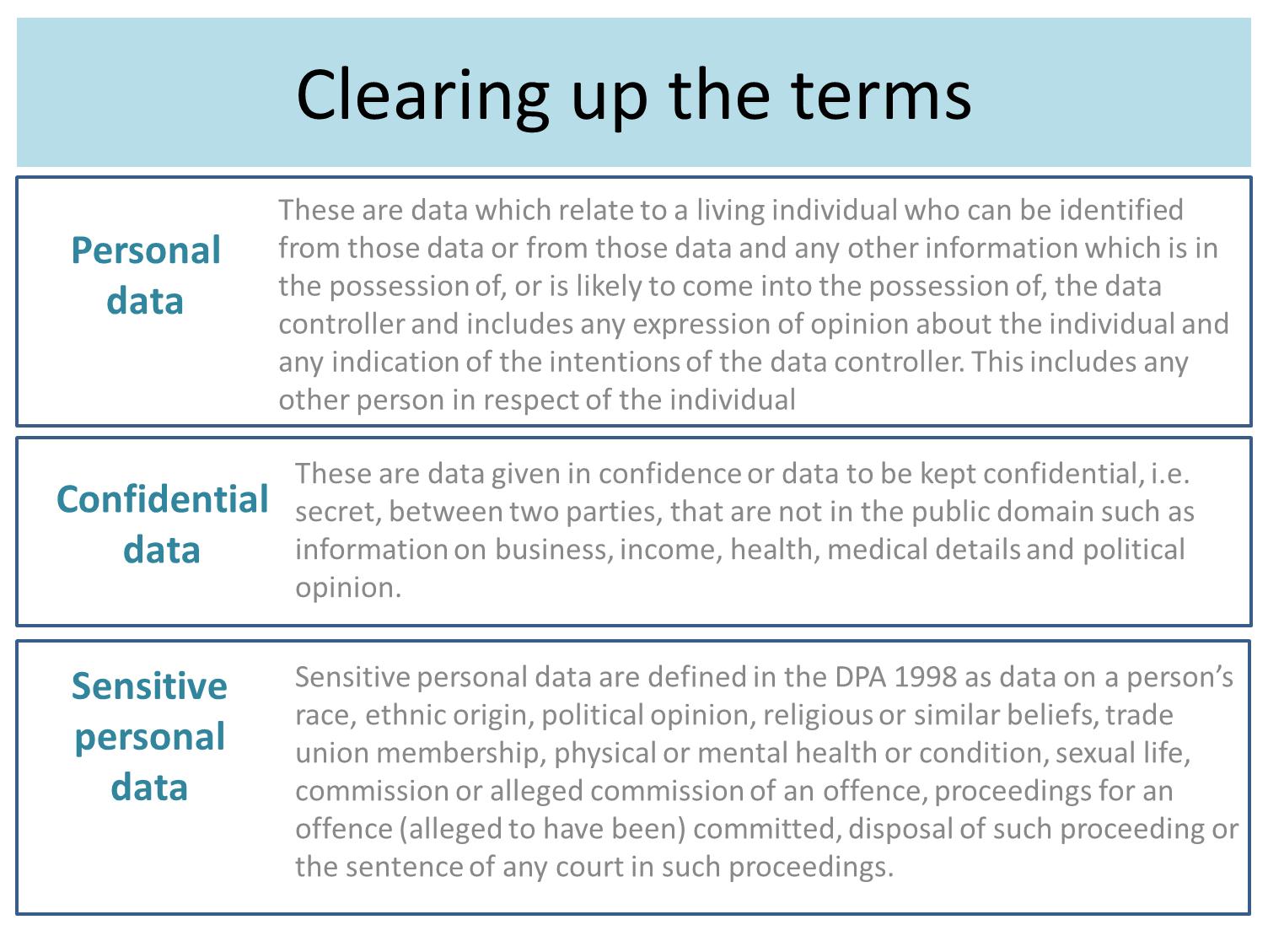
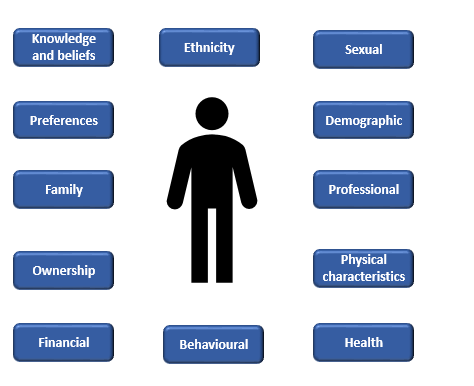

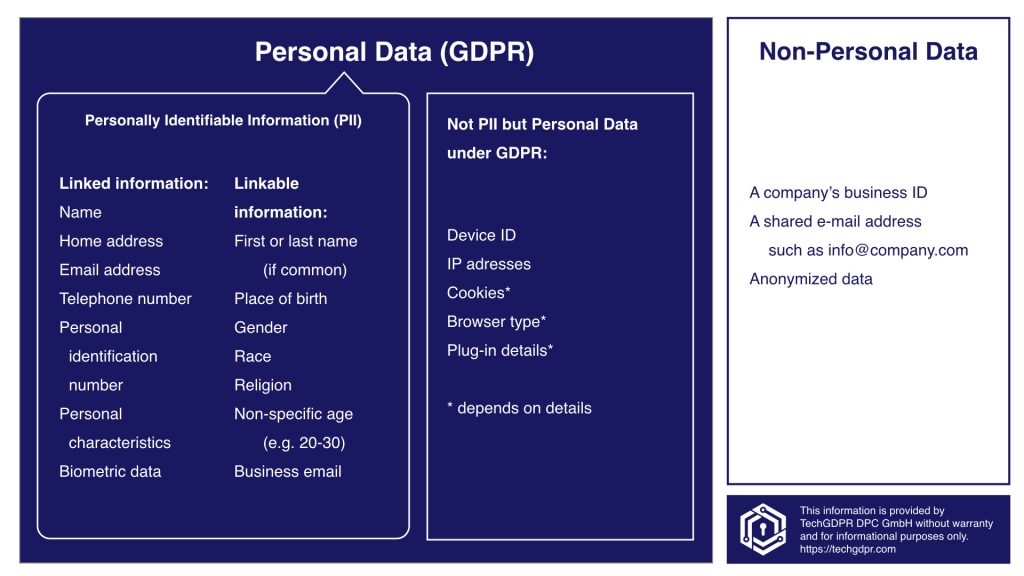
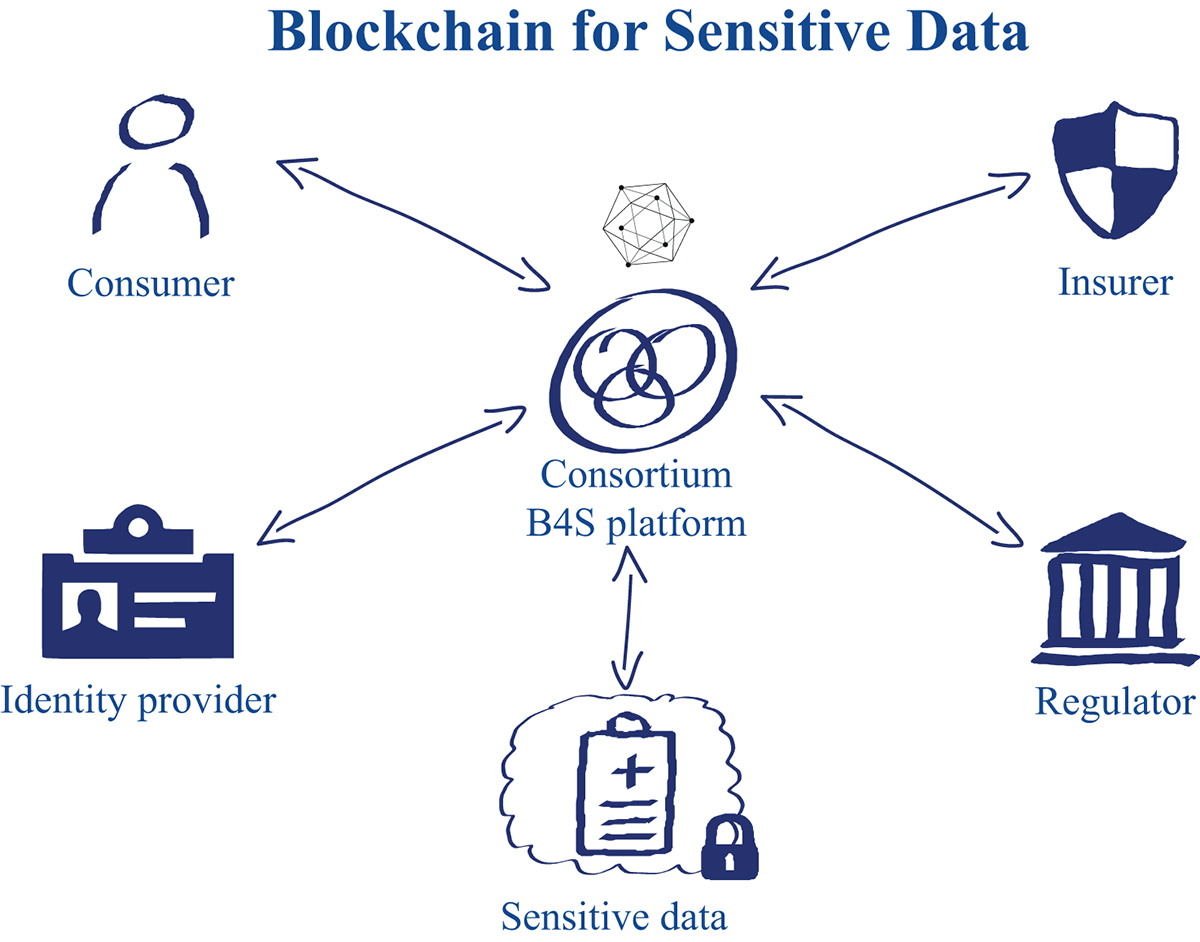
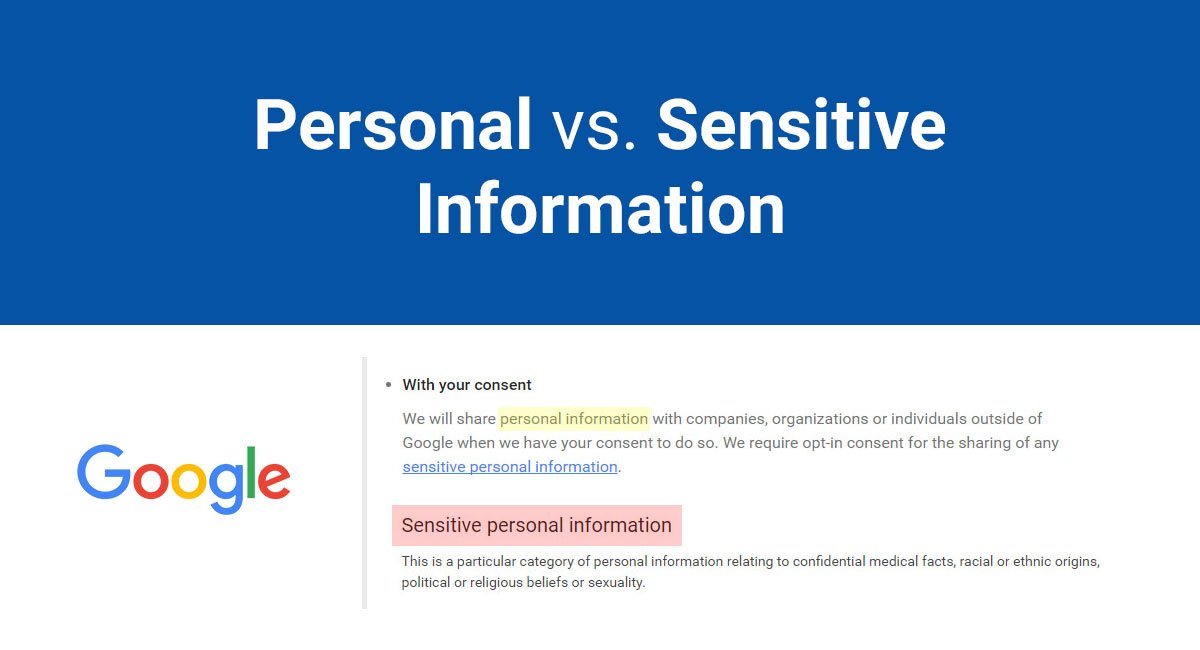
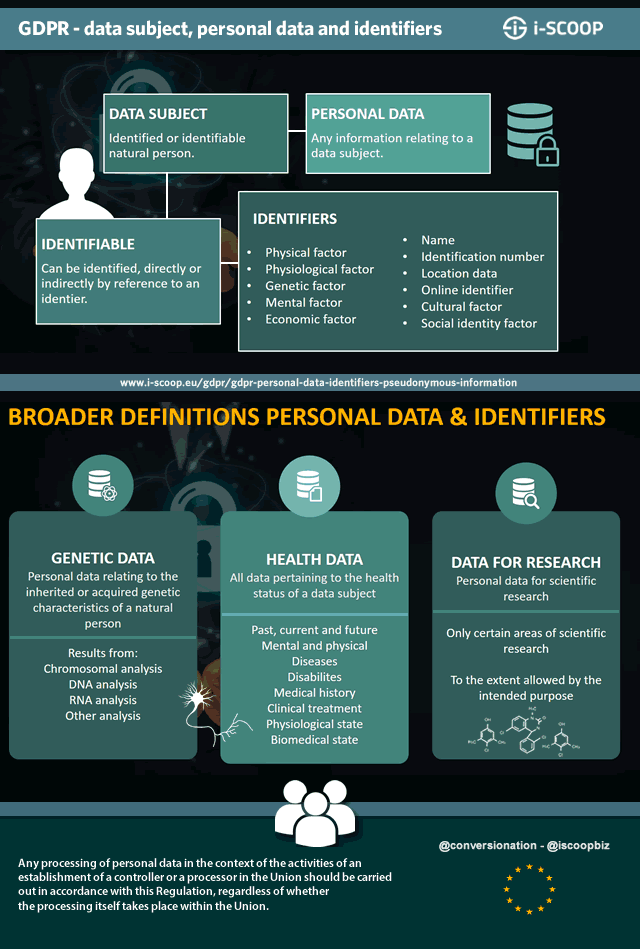


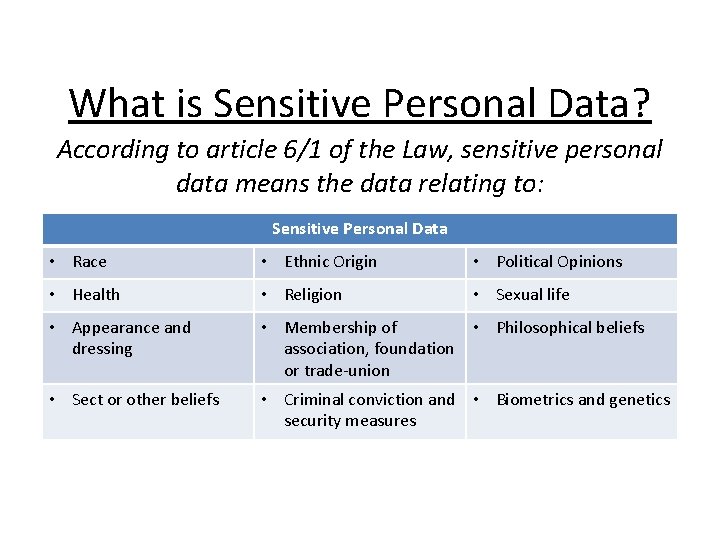




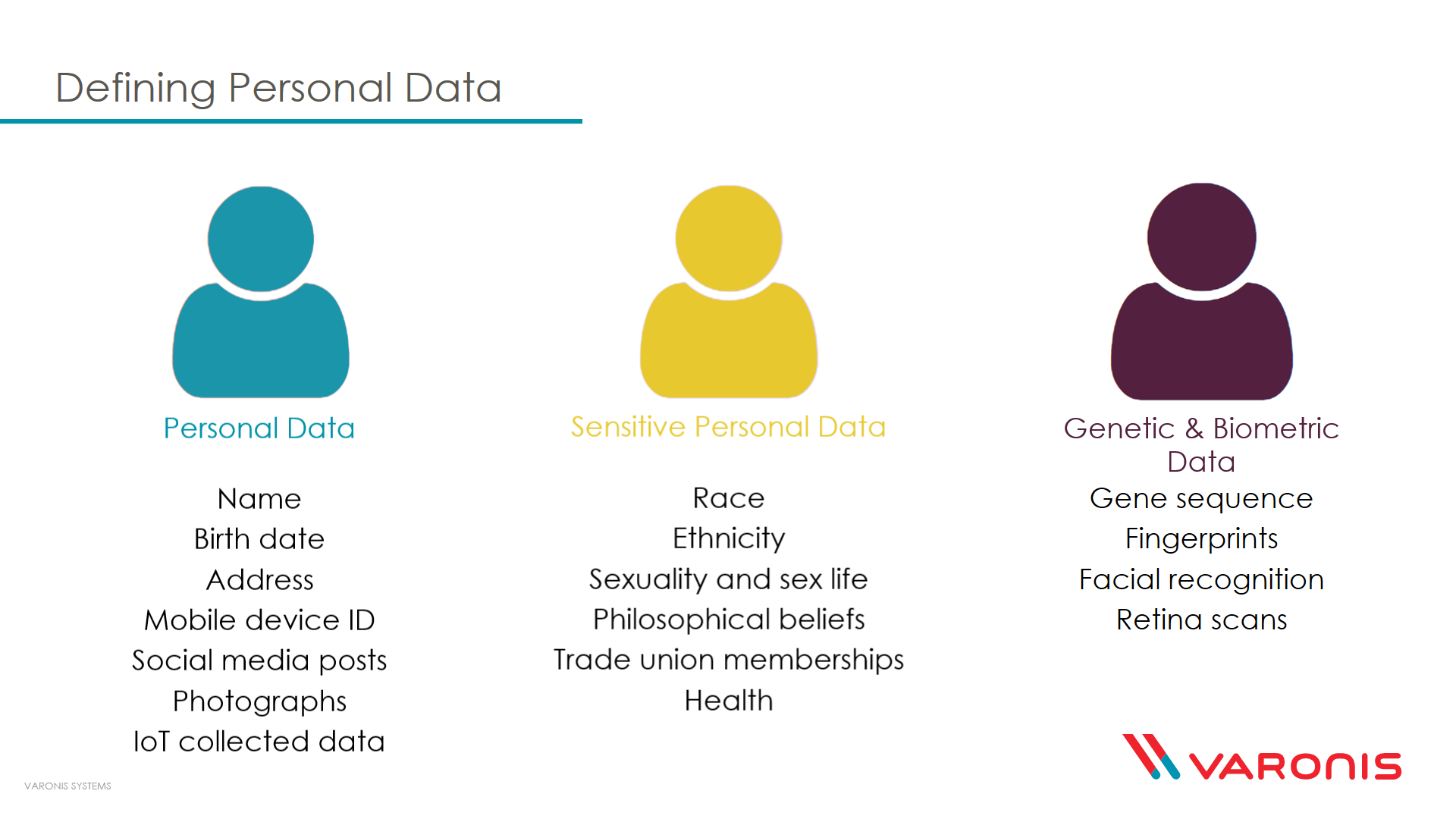
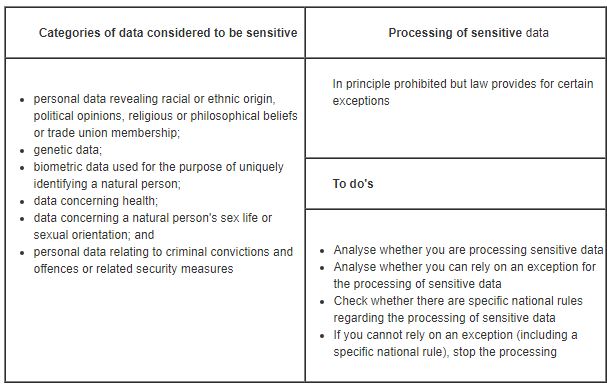

/GettyImages-166419812-612e00ba43f6445498228e6638adfc3a.jpg)